MISP | EN
MISP (Malware Information Sharing Platform) is an open-source threat intelligence platform that goes beyond indicators of compromise. It simplifies the sharing and utilization of threat information, fostering collaboration among organizations. With its emphasis on accessibility and interoperability, MISP enables seamless integration with other tools and platforms, making it a valuable asset for enhancing threat intelligence capabilities and collective defense against cyber threats.

CONNECTING THREAT INVESTIGATION AND THREAT INTELLIGENCE
Integrating MISP threat intelligence with the Defants AIR enhances threat detection, improves contextual understanding, supports proactive defense, and facilitates collaborative threat intelligence sharing.
This integration provides organizations with a more comprehensive view of potential threats, enabling quicker identification and response to security incidents while fostering collaboration within the cybersecurity community.
Integrations with Defants vSIRT
Enhanced Threat Detection
By integrating cyber threat intelligence feeds, Defants AIR identifies malicious indicators more effectively, enabling swift detection of potential threats.
Contextual Understanding
Cyber threat intelligence offers crucial context about threats, including adversary tactics and procedures, enhancing analysts' grasp of detected threats.
Proactive Defense
Access to up-to-date threat intelligence empowers organizations to defend against emerging threats proactively, bolstering overall cybersecurity resilience and reducing successful breaches.
Prioritization of Alerts
Cyber threat intelligence assists in prioritizing security alerts based on threat risk levels, enabling security teams to address critical threats promptly and enhance operational efficiency.
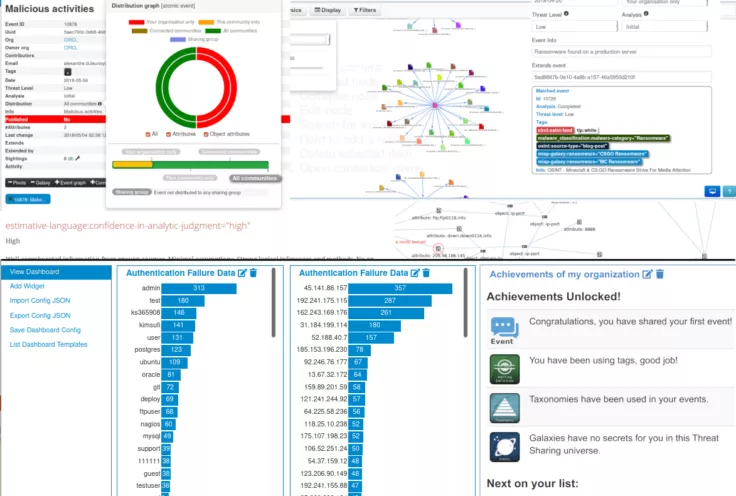
Automation : MISP enables structured storage of IOCs, facilitating correlation, automated exports for IDS or SIEM in STIX or OpenIOC formats, and synchronization with other MISPs, allowing effortless leveraging of data value.
Simplification : ISP prioritizes simplicity, ensuring ease of use in storing and utilizing threat information, maximizing data utility without overwhelming complexity.
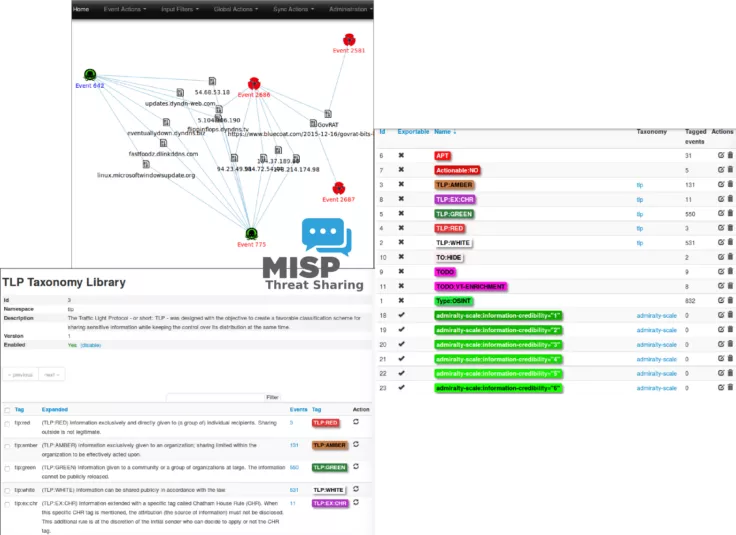
Collaboration : Sharing is central to effective attack detection. MISP simplifies sharing with trusted partners and trust-groups, enabling collaborative analysis and preventing redundant work. Join an existing MISP community to streamline sharing processes.
Comprehensive Threat Intelligence : MISP expands beyond Indicators of Compromise, offering metadata tagging, feeds, visualization, and integration with other tools via open protocols and data formats.
Enhanced Visualization : Accessing vast threat information via MISP Threat Sharing communities allows for superior data aggregation, elevating the understanding of how this data interconnects to tell a broader story. MISP transforms technical data into cyber threat intelligence, offering numerous visualization options for analysts to find insights efficiently.
Accessibility & Interoperability : The MISP Threat Sharing ecosystem emphasizes accessibility and interoperability. The software is free to use, with open standards for data format and API, and support available from both the community and professional services.
About MISP
MISP Threat Sharing (MISP) is an open-source threat intelligence platform that facilitates the sharing of indicators of compromise (IOCs) among organizations. It originated in 2011 as CyDefSIG and evolved into MISP, initially used by the Belgian Defence and later adopted by NATO.
Andras Iklody is the lead developer of MISP, which has expanded to cover not only malware indicators but also fraud and vulnerability information. It is funded by the European Union and the Computer Incident Response Center Luxembourg.
MISP integrates with various sources, including internal teams, intelligence sharing partners, and commercial intelligence sources like Symantec’s DeepSight Intelligence, Kaspersky, and McAfee.